User Impersonation
User impersonation allows administrators to temporarily sign in to Pomerium as another user or group within an organization. The impersonating user is subject to the access and authorization policies of the impersonated user.
Why impersonate a user?
In certain circumstances, it's useful for an administrative user to impersonate another user, like:
- Troubleshooting errors. If a user reports that they do not have access to a particular resource, you may want to impersonate that user in order to see what they see, to help diagnose any problems with the authorization policy.
- Making changes for an absent user. If a user is out of office, you could impersonate them to make changes for them while they're away.
- Testing policies, routes, or other settings. As an admin, you can build authorization polices and test them out as another user to preview what other users will see depending on the permissions you grant them.
How to impersonate a user
You can impersonate a user by using the Console GUI or creating a Service Account.
Impersonate a user in the Console
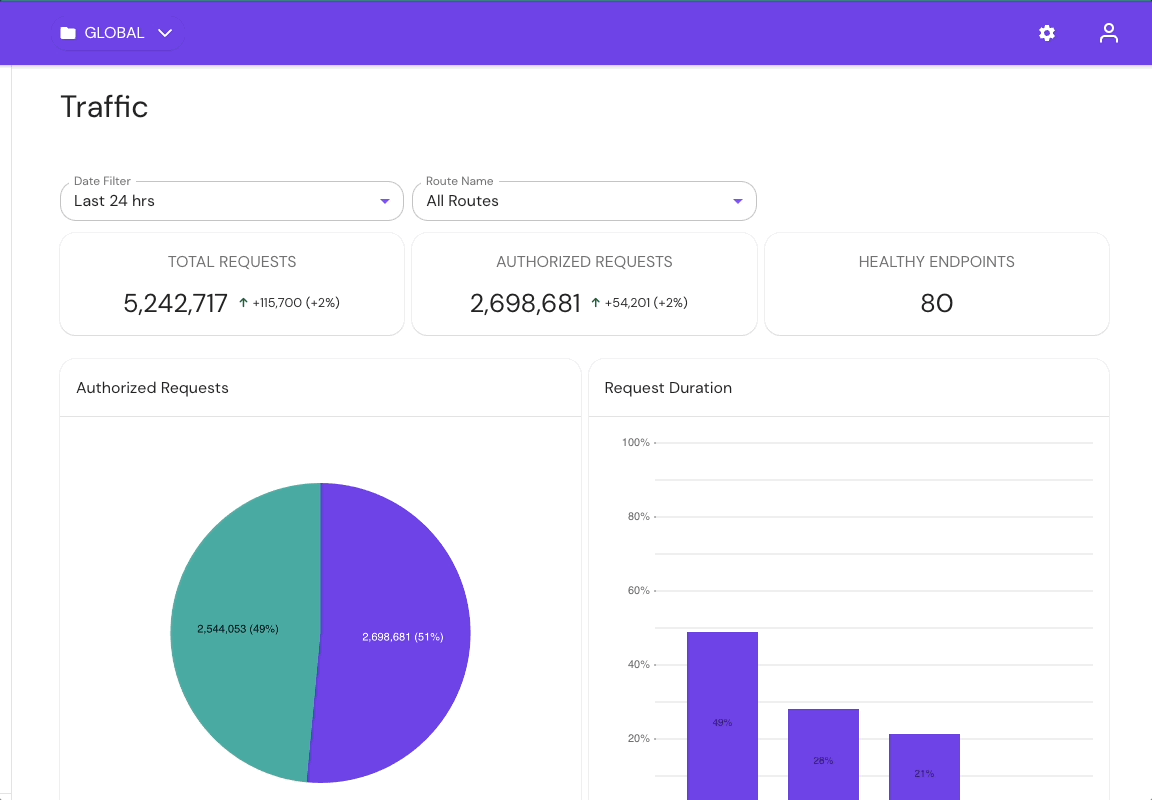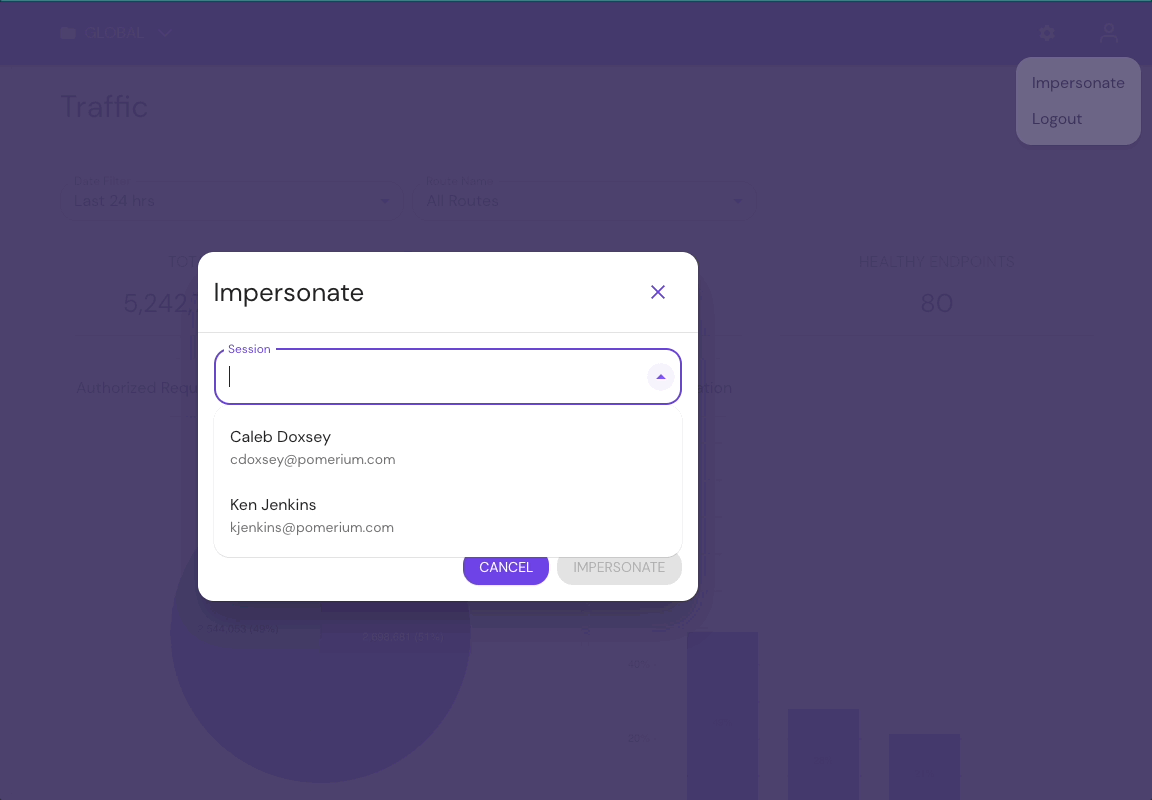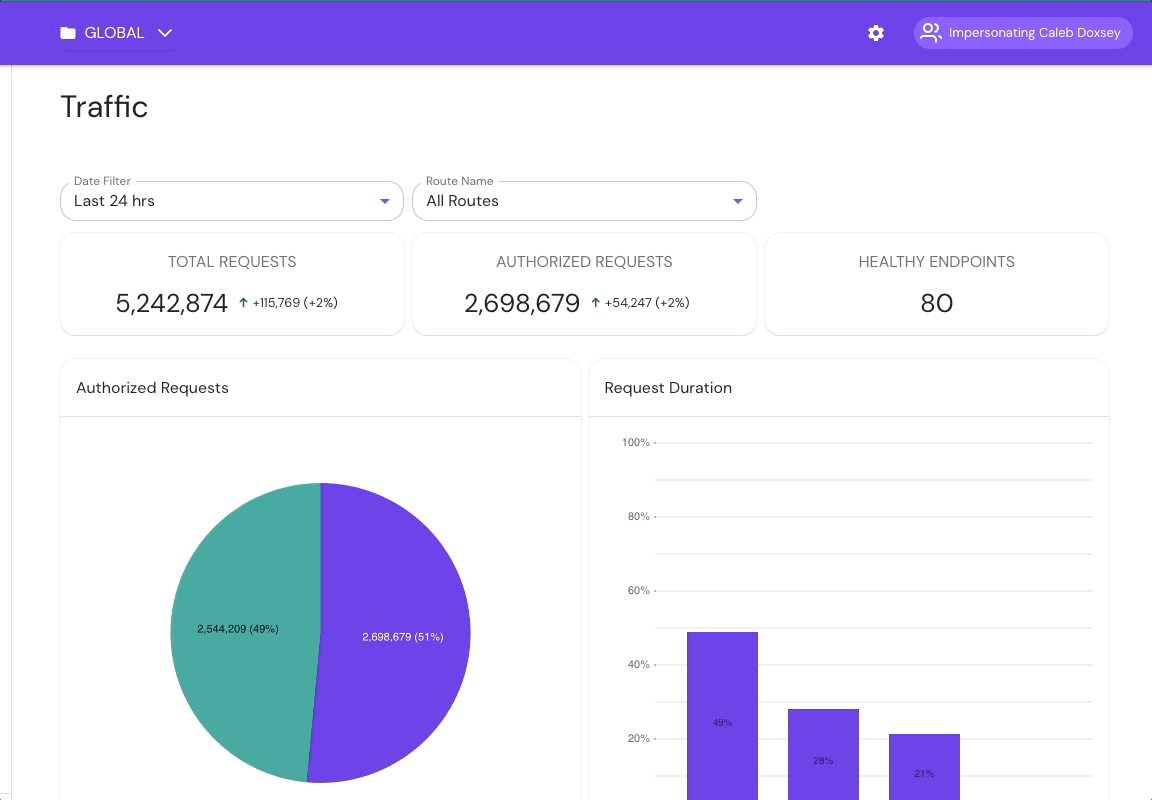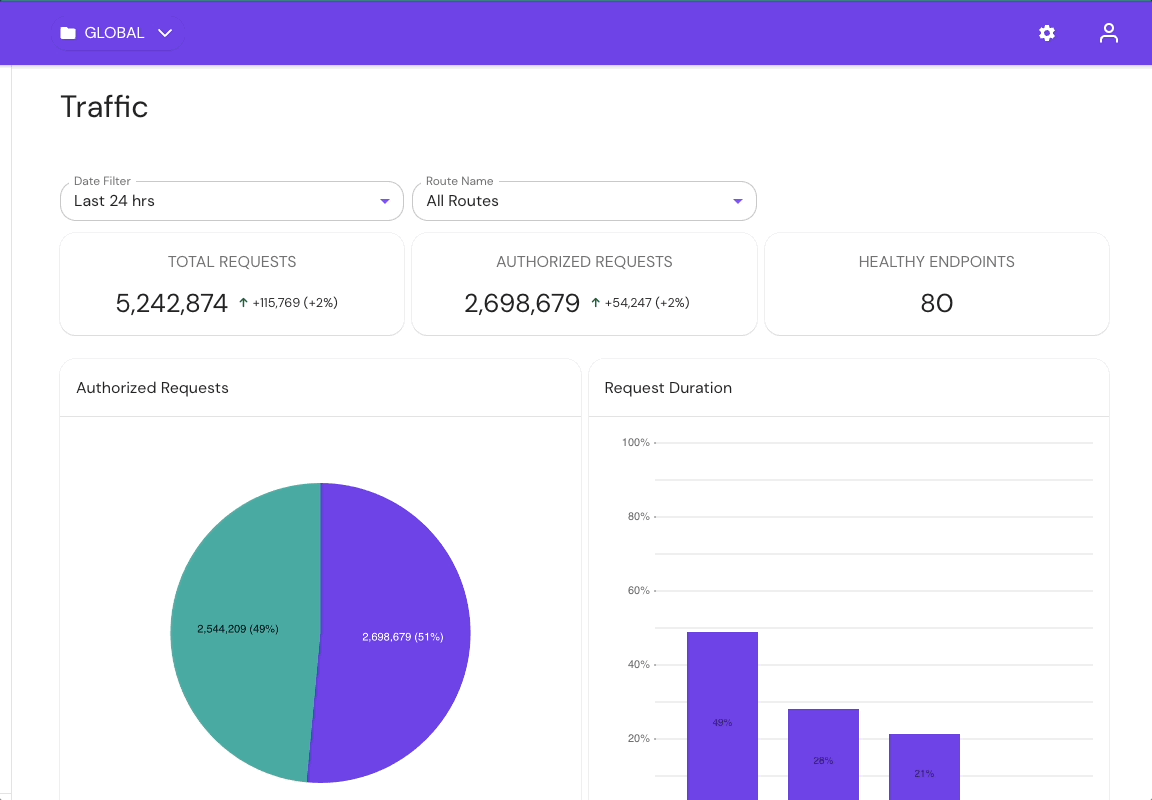
- In your Console, select the Logout icon
- Select Impersonate
- In the Session dropdown, select the user you want to impersonate
- Select Impersonate
When you're finished impersonating the user, select Unimpersonate.
Impersonate a user with a Service Account
Create a service account:
Before you begin, confirm you are in the correct Namespace. A service account can only be used in the Namespace it was created in, including its children Namespaces.
- Go to Service Accounts
- Select Add Service Account
- Select User ID, enter an optional Description, and set the expiration time
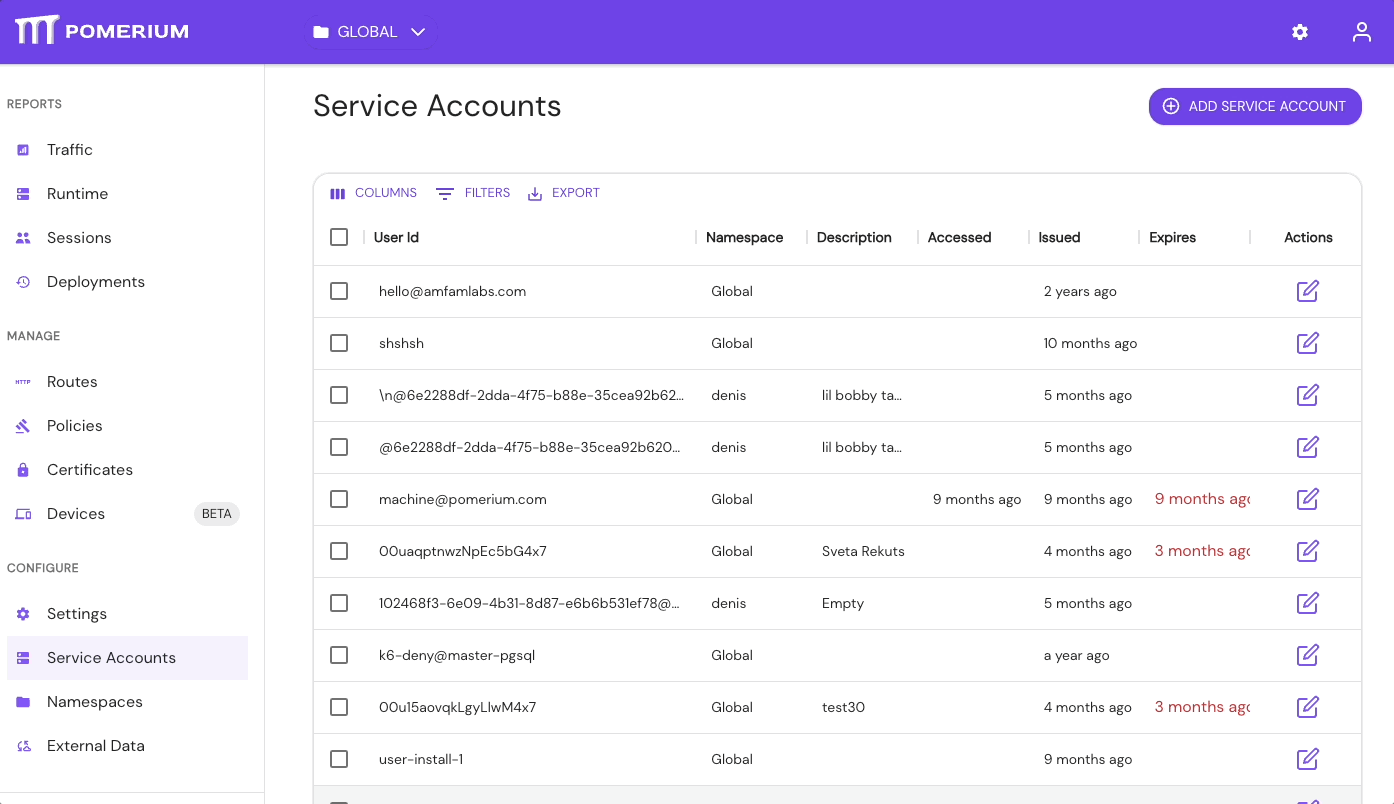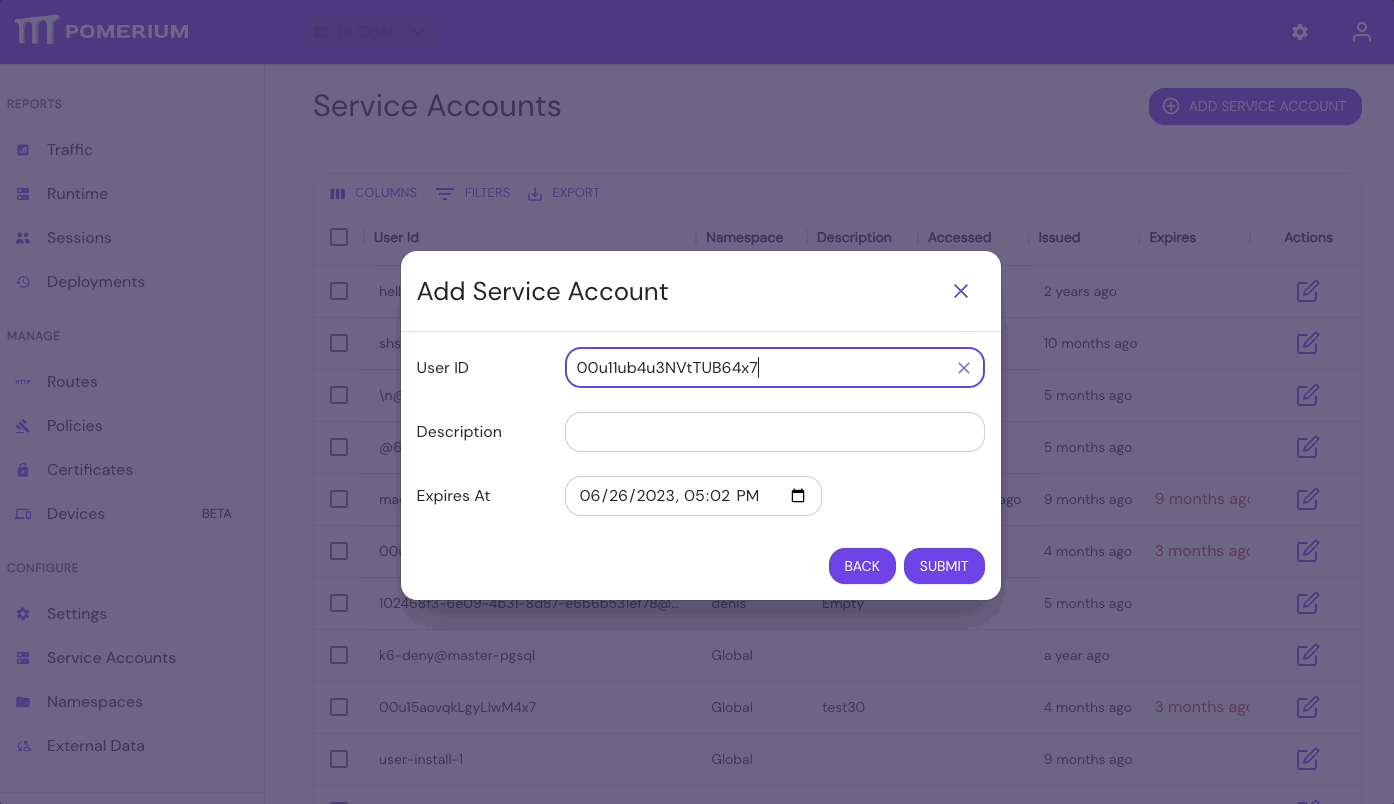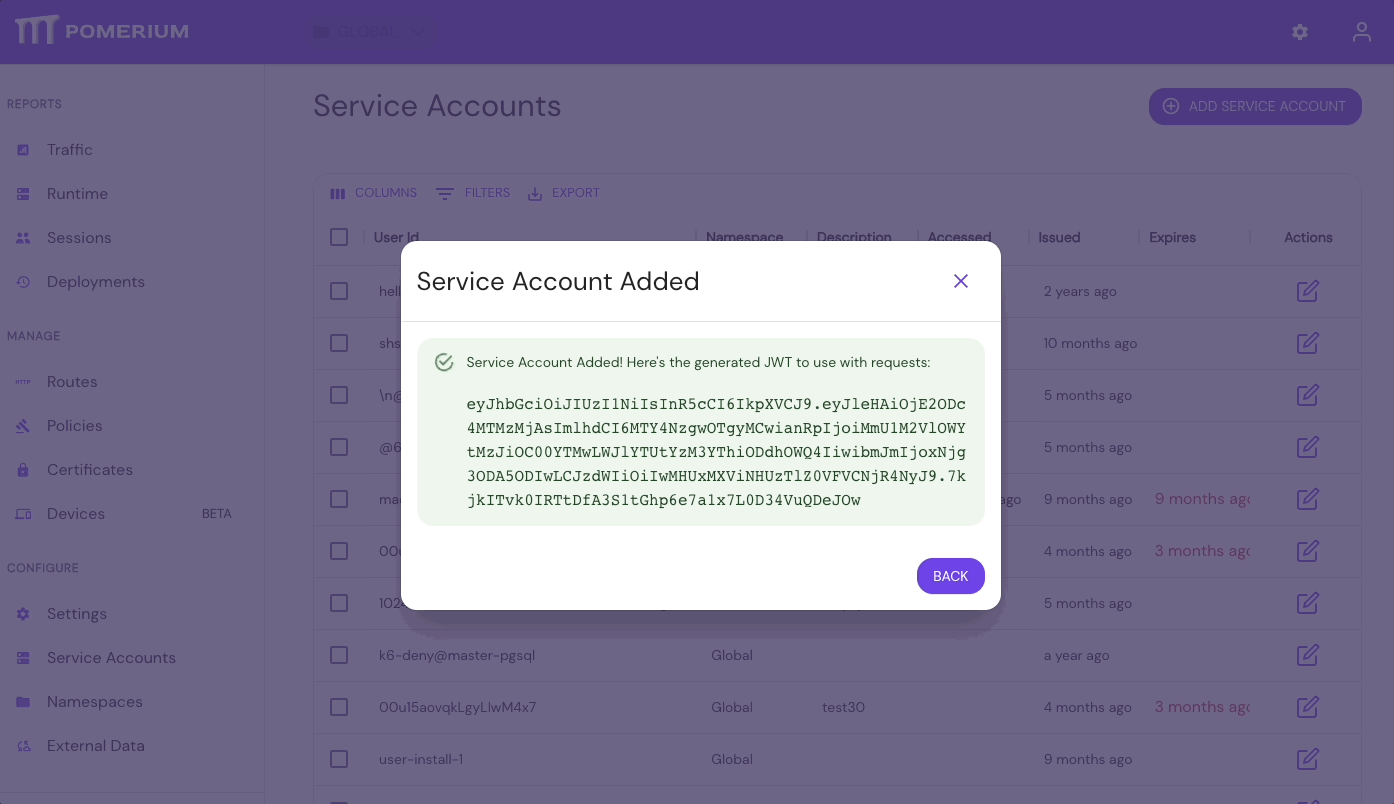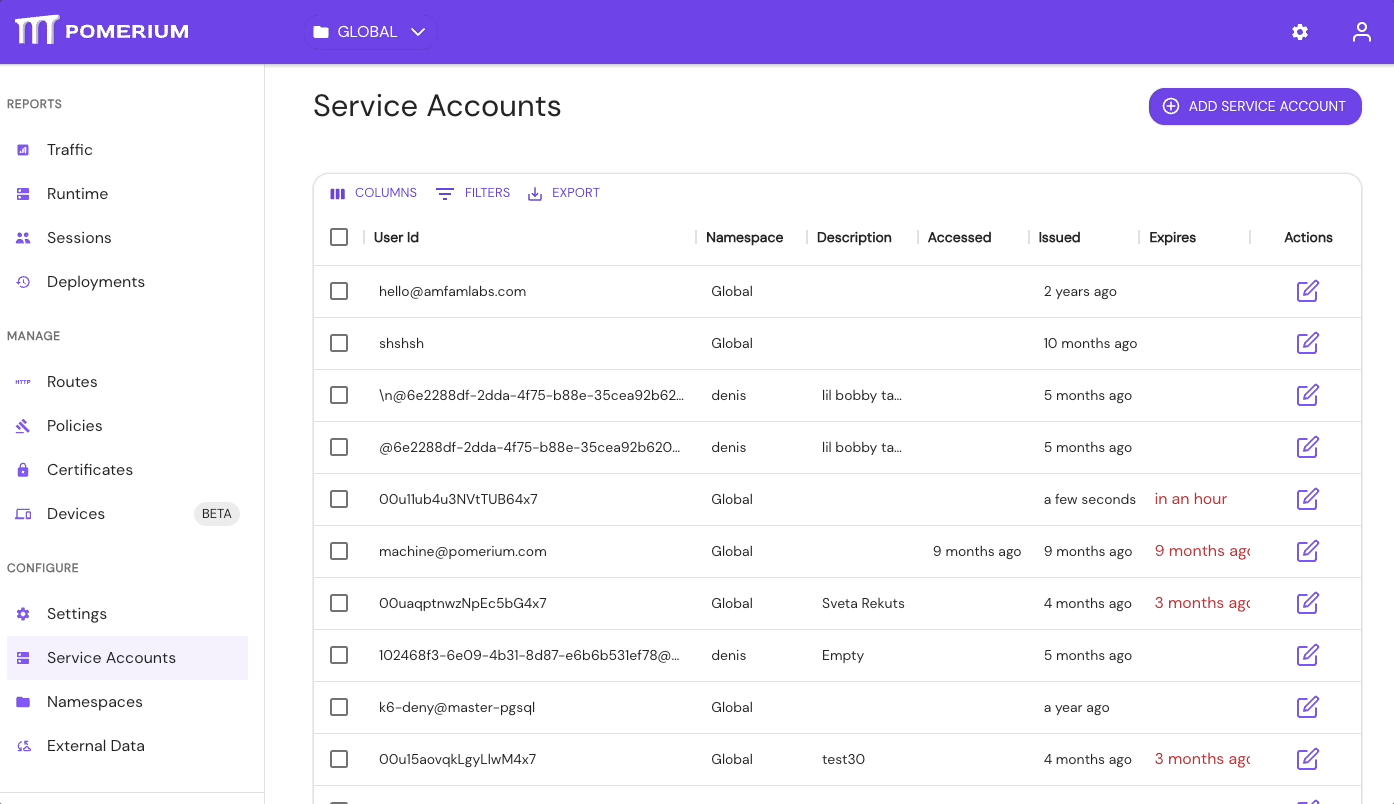
- Save the Service Token JWT
Add the Service Account to a policy:
- Go to Policies > NEW POLICY
- In the Builder tab, select ADD ALLOW BLOCK
- In the Criteria field, select User
- In the Search Users field, select the Service Account
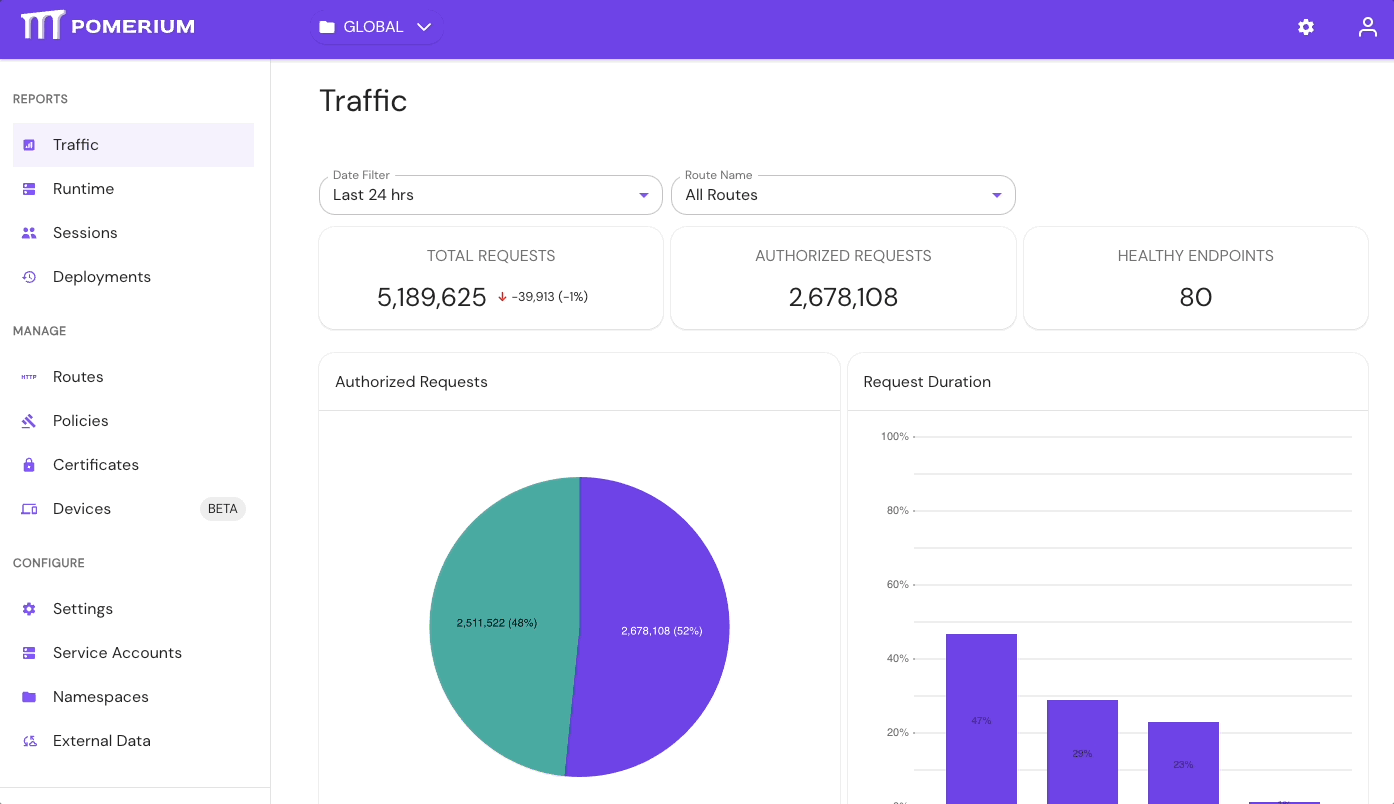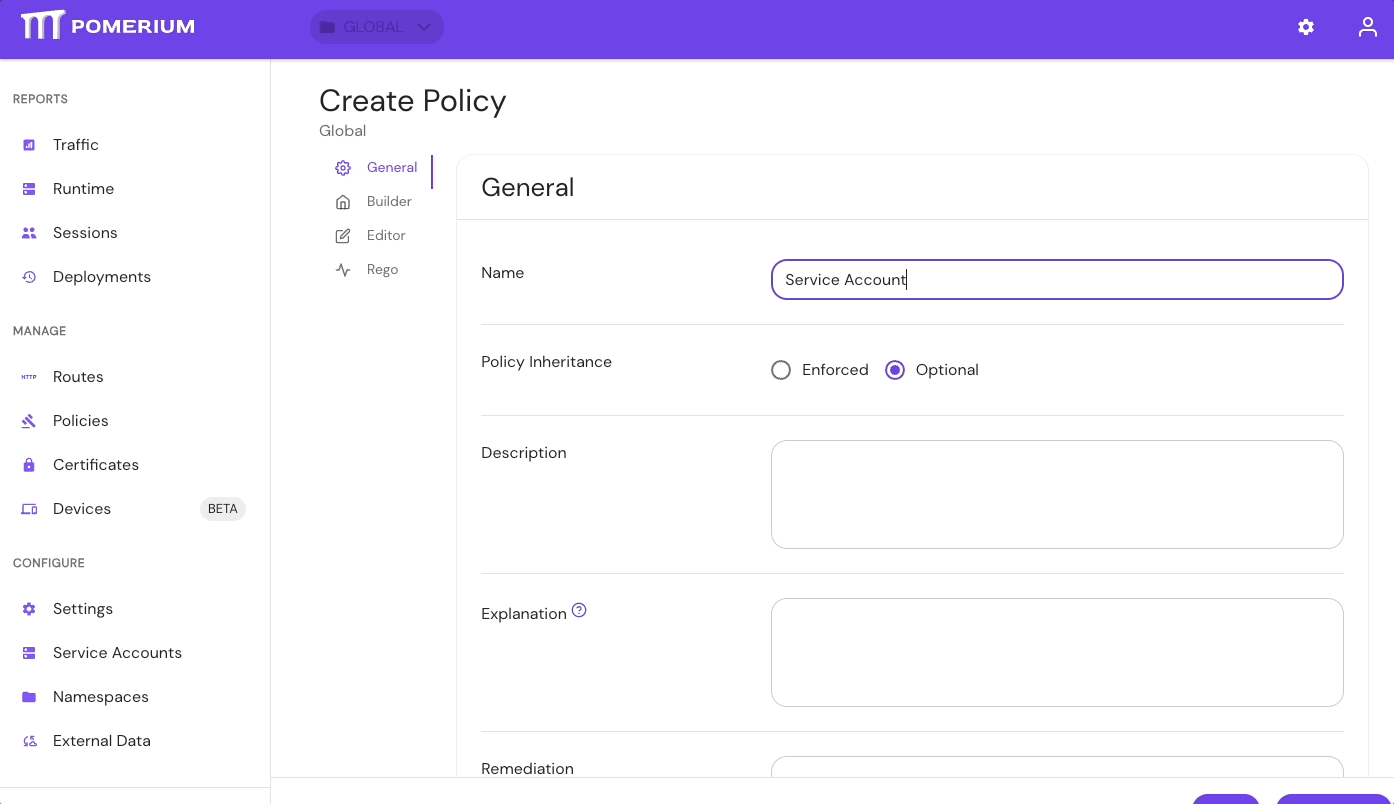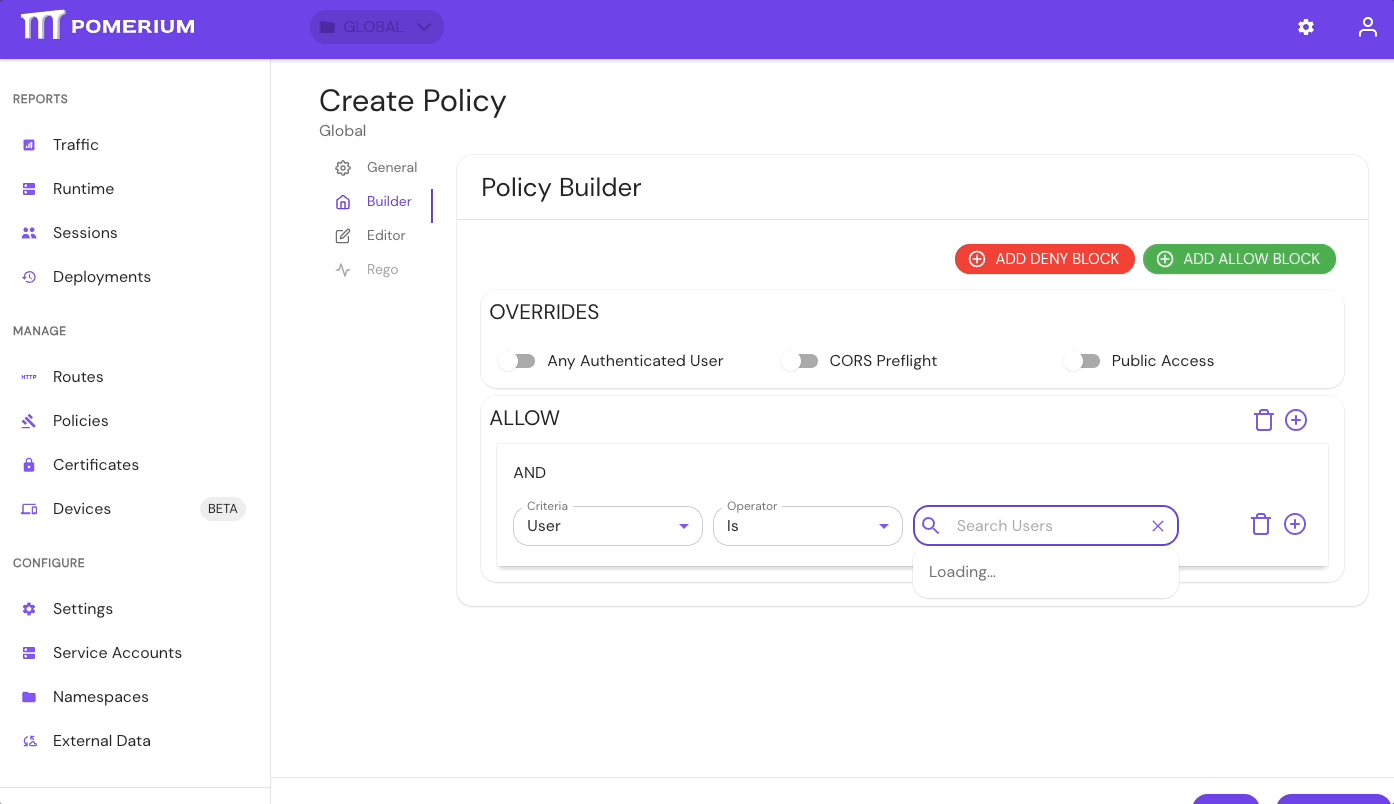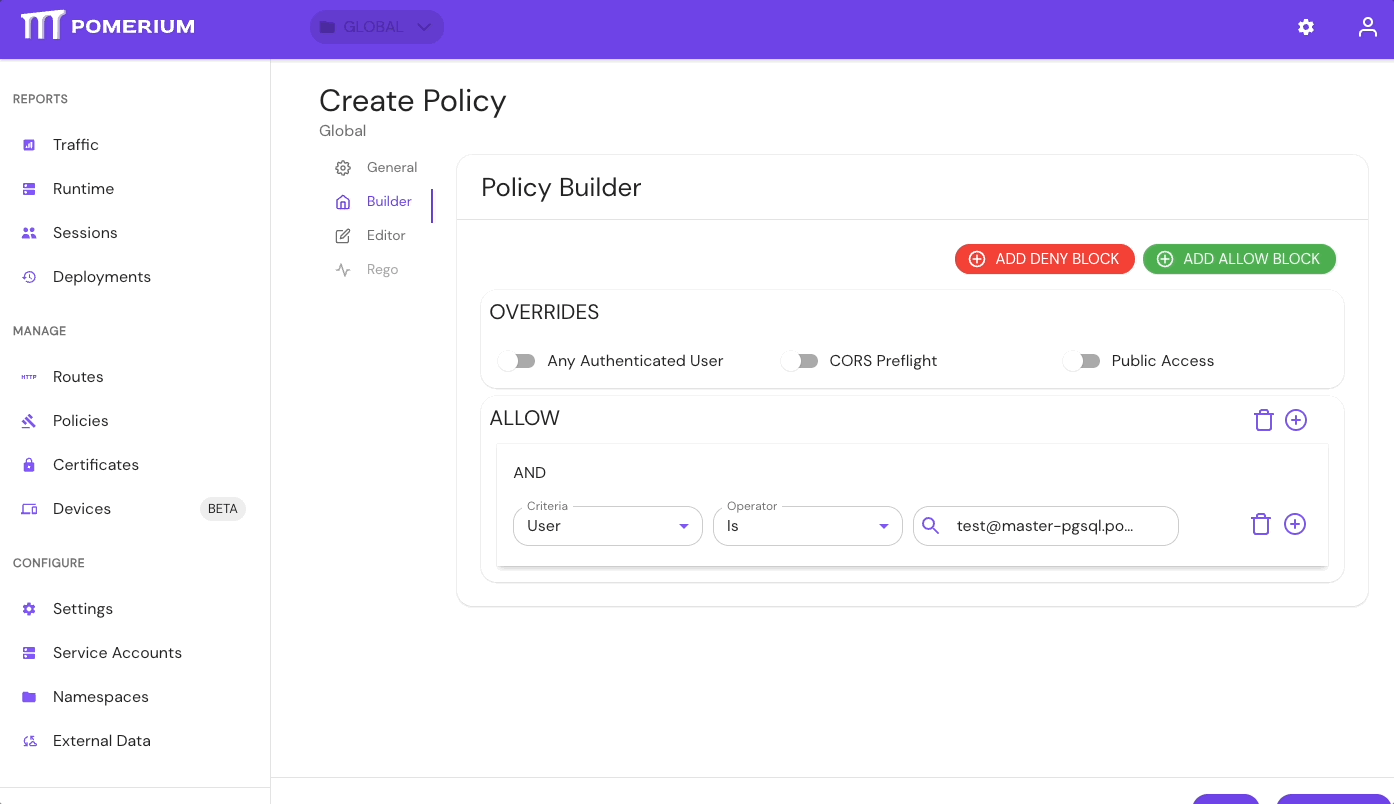
Now, you can apply the policy to a route and access it using any of the following header schemes:
Authorization: Bearer Pomerium-${pomerium_jwt}X-Pomerium-Authorization: ${pomerium_jwt}Authorization: Pomerium ${pomerium_jwt}